Web Application Pentesting – What It Is and 5 Best Tools Used
The objective of web application pen-testing is to discover any flaws that might be used by attackers. Web app pentesters are able to do this because they have the necessary knowledge and skills to understand what makes web applications work on a fundamental level, as well as having access to tools for exploiting those weaknesses. In this article, we mention some of the tools you can make use of to test and assess the vulnerabilities within your web application!
What Is Web Application Security?
Web application pentesting is a process of testing the security, functionality, and accessibility of web applications. It often revolves around assessing how secure an organization’s website is from cyberattacks by hackers. Web application security is a subset of general information technology (IT) security. It focuses on the protection and safekeeping of web applications. They are related to business activities carried out through websites or other electronic means. The importance of protecting these applications cannot be understated. They store critical data that can impact the safety and well-being of people around the world.
Web applications handle and store a wide range of personal data, including credit card numbers, social security numbers, biometric identifiers like fingerprints and faces, and more. Identity theft, fraud, and other serious crimes could result if this information fell into the wrong hands. So, what can one do to keep these apps safe? Web application pentesting is one way to ensure that web applications are safe for use. However, before the pen-testers can begin their work, they need to understand what makes these types of applications vulnerable in the first place.
Understanding Weaknesses Within Web Applications
Web app vulnerabilities stem from two different places: mistakes made by developers while writing code and backend configuration errors/misconfigurations. The first type of vulnerability is called a “code flaw”, while the second one goes by the name of “configuration error”.
There are four main types of vulnerabilities that can be found in web applications, including:
- Cross-Site Scripting (XSS)- occurs when a web application sends user input to a browser without first validating or encoding it. This allows attackers to inject malicious code into the website, which could lead to identity theft and other cybercrimes.
- Injection Vulnerabilities- When an attacker is able to inject fraudulent data into the application in order to execute unauthorized instructions, these flaws occur. This could result in information disclosure, loss of funds, or even a takeover of the web application itself.
- Broken Authentication and Session Management- When authentication and session management technologies in web applications are not operating as intended, these sorts of flaws occur. This could result in attackers being able to access or misuse sensitive data, take over other users’ accounts, or even gain full control over a website’s backend
- Insufficient Authorization and Access Control- these vulnerabilities are caused when an application does not properly check whether a user is authorized to access certain data or resources. This could lead to unauthorized users gaining access to sensitive information or taking over the account of an authorized user.
The OWASP Top Ten Vulnerability List contains all the details on these issues. It’s crucial to understand how they function so that you can safeguard your online applications from them.
Types Of Web Application Pentesting Done By Pen Testers
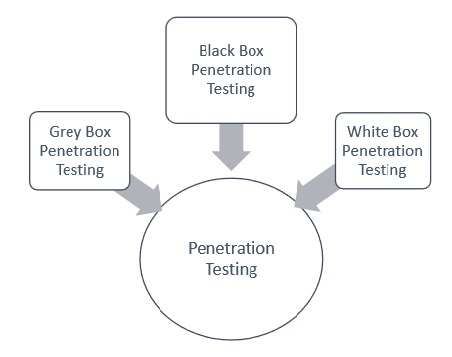
Now that we have some idea about what web application pen-testing is and what types of tools can be used for this task, let’s take a look at the different types of pentesting that can be done. The first type is known as “white-box testing”, which means that you have unlimited access to source code and other data about the application before doing your penetration test/pentest. In order to properly do white-box web app pen testing, you need to have a deep understanding of the application and how it works.
Another type is grey box testing. This means that pentesters only have limited access to app data before they begin their penetration test/pentest. Gray-box web application pen testing can be performed in two different ways: with publicly available information about the target or with information that has been provided by the target organization. The last type of pen-testing is black-box testing, which is the most common type. In black-box pentesting, pentesters have no access to any data about the application whatsoever before they start their assessment. Each of these types of pentests can be used in different ways to test the security of web applications.
5 Best Tools For Web Application Pentesting
The five best tools for web application pentesting are
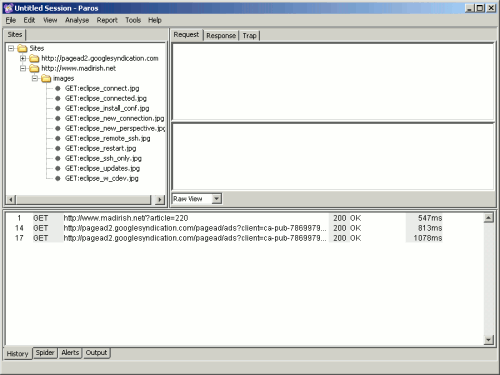
Paros Proxy
This proxy is based on Java and can be used to test a wide range of web applications. It may be utilized for both black box and white box testing. It also comes with a built-in webserver to help you generate your own code on the fly or steal data from other sites.
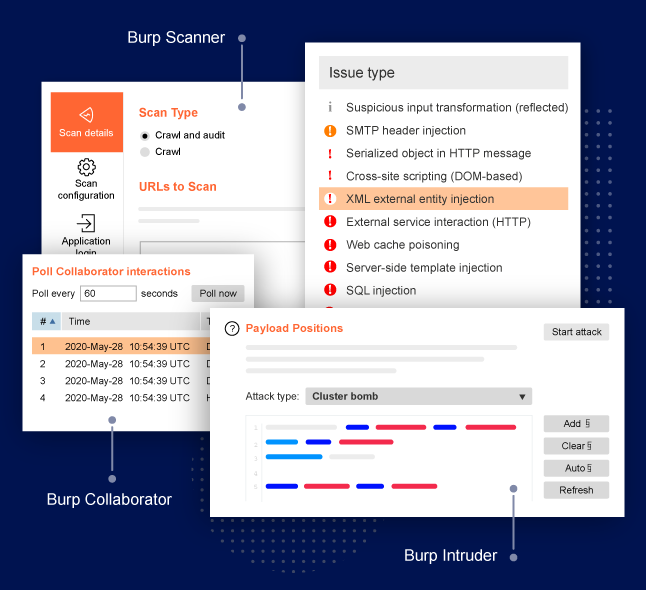
Burp Suite Pro
An integrated platform designed to test web apps with a suite of tools that are available in one single program. This includes the intruder tool. It is for performing automated customized attacks against web applications.
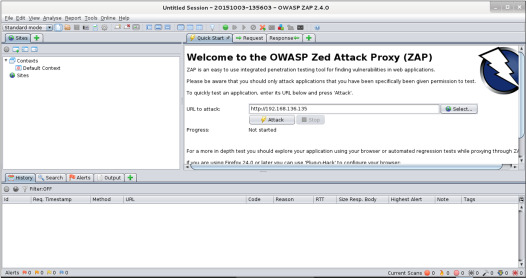
OWASP Zed Attack Proxy (ZAP)
This is a free, open-source web application penetration testing software that may be used to check the security of online applications. It includes features like spidering, scanning, and a proxy server to intercept traffic from the target app.
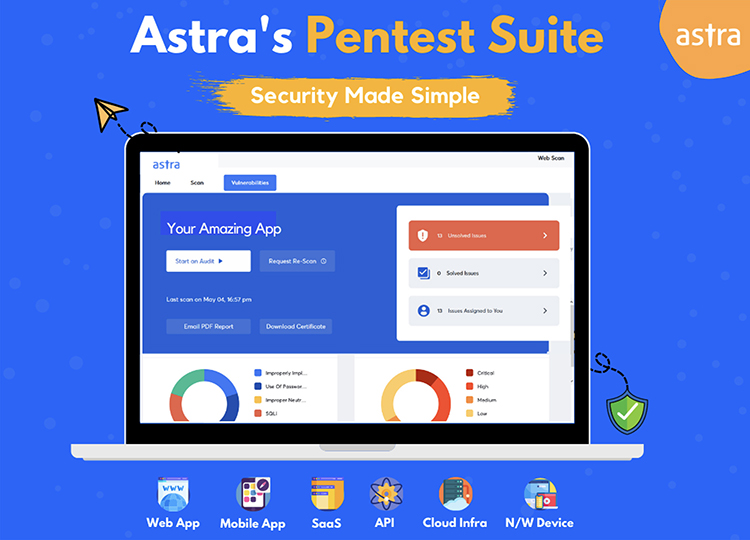
Astra Pentest
This is a web application security scanner for scanning for vulnerabilities in the client-side code of applications. The benefits of choosing Astra include easy installation and use of the tool, which does not require any programming or scripting skills.
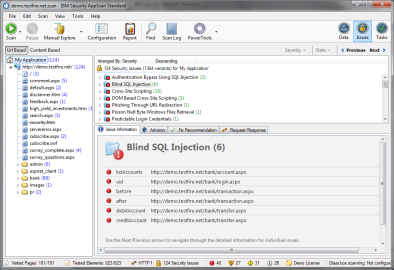
AppScan Standard Edition
IBM’s commercial web application security scanner can be used to find vulnerabilities in applications like OWASP Top Ten, buffer overflows, and cross-site scripting. These are just a few of the many tools that are available for pentesting web applications. Each tool has specific characteristics and a distinct target audience.
Web Application Pentesting – Conclusion
In this post, we have looked at what web application pen-testing is and some of the tools for exploiting vulnerabilities in these types of applications. We also took a look at the different types of pen tests and their performance.